How to Protect Your Passwords After the 16 Billion Credential Breach
Updated • 16 min read
Introduction to the Breach
In June 2025, cybersecurity researchers uncovered a record-breaking data breach involving over 16 billion stolen login credentials. Several massive datasets (around 30 in total) were found exposed on the web, containing usernames, passwords, and even authentication tokens for a huge range of online services. Nearly every major platform has been affected – including Apple, Google, Facebook, GitHub, Telegram, and even government portals. Unlike many past leaks, this trove appears to consist of freshly stolen data (likely harvested by infostealer malware) rather than old, recycled breaches. In other words, many of these passwords could still be valid, creating an extremely dangerous situation. Security experts warn that attackers now have an unprecedented “blueprint for mass exploitation,” enabling widespread account takeovers, identity theft, and targeted phishing scams using the exposed credentials.
What was exposed? Essentially everything: email addresses, passwords, and even the exact websites each password is for. That means a hacker with access to this breach data doesn’t have to guess where a password might work – they know exactly which account it goes to. For all of us, this is a wake-up call to double down on password security. Below, we’ll explain why weak or reused passwords put you at risk, how to check if you were affected, and steps you can take right now to secure your digital life in the aftermath of this incident.
Why Reused or Weak Passwords Are Dangerous
Reusing passwords on multiple sites or choosing weak, easy-to-guess passwords can turn a single breach into a cascading security nightmare. In fact, an estimated 81% of hacking-related breaches leverage stolen or weak passwords. If you’ve been using the same password across different accounts, a hacker who obtains that one password from a breach could gain access to all those accounts – a technique known as credential stuffing. This is exactly what happened to one victim of an Adobe breach years ago: attackers grabbed his one password and were able to break into his email and other services he used it on.
Weak passwords (such as “123456”, “password”, or common words and phrases) are equally dangerous. Cybercriminals use automated tools to guess or brute-force simple passwords in seconds. Short passwords or those composed of dictionary words can be cracked almost instantly with modern computing power. Once cracked or leaked, a weak password offers attackers an open door into your account. In the context of a breach as large as 16 billion records, any accounts protected by weak or reused passwords are essentially low-hanging fruit for hackers. The bottom line: if your passwords aren’t strong and unique, one breach can lead to many victims.
How to Check If Your Credentials Were Exposed
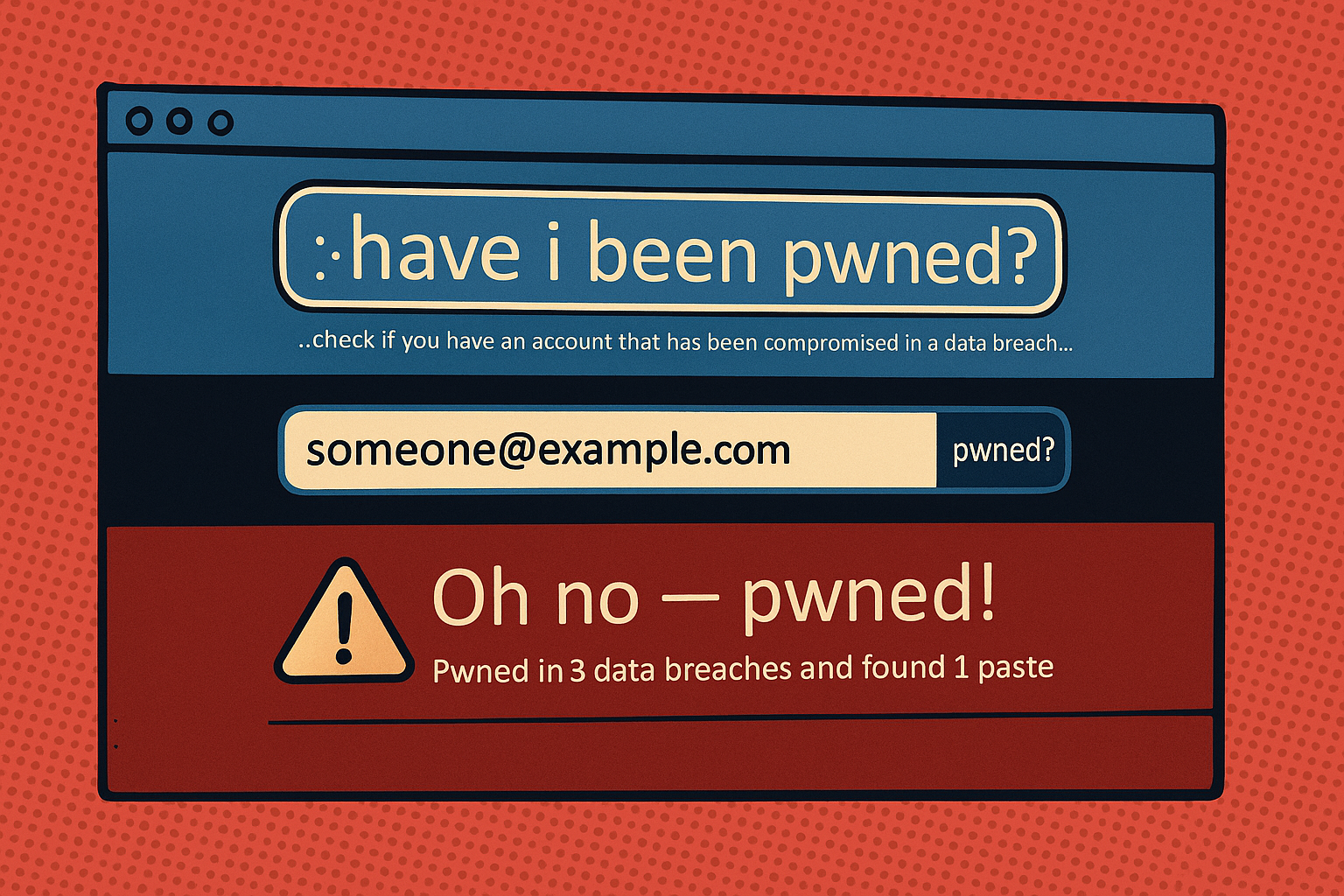 Not sure if your accounts are in this mega-breach (or any other)? Fortunately, there are free tools that let you check. The most popular is Have I Been Pwned (HIBP) – a website run by security expert Troy Hunt that compiles data from breaches and lets you search for your email or username. Simply go to the HIBP site, enter your email address, and it will tell you if that email appears in any known data breaches (and which ones). If you register your email, HIBP can also notify you of future breaches where your data turns up. This is an easy way to get an early warning if your credentials are compromised.
Not sure if your accounts are in this mega-breach (or any other)? Fortunately, there are free tools that let you check. The most popular is Have I Been Pwned (HIBP) – a website run by security expert Troy Hunt that compiles data from breaches and lets you search for your email or username. Simply go to the HIBP site, enter your email address, and it will tell you if that email appears in any known data breaches (and which ones). If you register your email, HIBP can also notify you of future breaches where your data turns up. This is an easy way to get an early warning if your credentials are compromised.
In addition to HIBP, some other services offer similar “breach check” features. For example, the cybersecurity news site Cybernews provides a Personal Data Leak Checker tool (accessible on their website) where you can search by email address to see if your data has been leaked. Firefox and Chrome browsers have built-in breach alerts as well (they will warn you if a password you saved was found in a known leak). Using these tools proactively is wise. If you discover your email or password in a breach, you can immediately take action (more on that in Section 7). And even if you’re not affected by this particular 16 billion credential leak, it’s a good habit to occasionally check your status – large breaches are sadly common.
Tip: HIBP also offers a feature called “Pwned Passwords”, where you can safely check if a specific password has ever appeared in a breach (without revealing your actual password). This can be useful if you’re curious about an old password’s exposure – though if a password is old or weak, you should change it regardless of whether it shows up.
Best Practices for Password Safety
Knowing the threat is only half the battle – it’s crucial to strengthen your passwords and overall login security before attackers strike. Here are some best practices to protect yourself:
- Use Strong, Unique Passwords: Every account should have its own password, and it should be hard to guess. A strong password is typically at least 12 characters long, includes a mix of uppercase and lowercase letters, numbers, and symbols, and doesn’t contain easy-to-find personal info (like your name or birthdate). Importantly, do not reuse passwords on different sites. Unique passwords ensure that if one account is breached, the rest stay safe. Yes, that means you’ll have a lot of passwords – but we’ll discuss tools to manage them in a moment.
- Enable Multi-Factor Authentication (MFA): MFA (also called two-factor authentication or 2FA) adds an extra layer of security on top of your password. When MFA is on, logging in requires a second step – usually a temporary code from an app (like Google Authenticator, Authy, etc.) or a text message, or a physical security key. This means even if someone knows your password, they can’t get into your account without that second factor. Turn on MFA wherever it’s available (especially for email, banking, and social media). It’s one of the most effective ways to stop hackers – in the 16 billion credential scenario, stolen passwords alone wouldn’t be enough to breach an MFA-protected account.
- Avoid Reusing Passwords Across Sites: This bears repeating because it’s so important. Using the same password on multiple accounts greatly amplifies the damage from any single breach. For example, if your one favorite password is exposed in a breach, attackers will promptly try it on all major sites (a Facebook password reused on Gmail, Dropbox, etc.). Use a different password for every account. That way, a breach at one service won’t automatically compromise others. Yes, it’s tough to remember dozens of logins – that’s exactly why password managers exist (see next section).
- (Bonus) Be Mindful of Phishing: Even the strongest passwords won’t protect you if you’re tricked into giving them away. Be cautious with emails or messages that ask you to “confirm” your password or login details, especially if they claim to be related to this breach. Scammers often capitalize on big news like a large breach – you might get an email that looks like it’s from Apple or Facebook about “security issues” prompting you to log in. When in doubt, don’t click links in emails; go directly to the service’s official website and log in there. Always ensure the URL is correct before entering credentials.
Overview of Top Password Managers
 The best way to handle strong, unique passwords for every site (without going insane) is to use a password manager. Think of a password manager as an encrypted vault that stores all your login credentials. You lock it with one master password (and/or other authentication), and the manager takes care of remembering all your individual passwords – often it can generate long random passwords for you, auto-fill them on websites, and sync them across your devices. By using a password manager, you only need to remember one password while achieving unique, complex passwords everywhere.
The best way to handle strong, unique passwords for every site (without going insane) is to use a password manager. Think of a password manager as an encrypted vault that stores all your login credentials. You lock it with one master password (and/or other authentication), and the manager takes care of remembering all your individual passwords – often it can generate long random passwords for you, auto-fill them on websites, and sync them across your devices. By using a password manager, you only need to remember one password while achieving unique, complex passwords everywhere.
There are many password managers out there, but here is an overview of a few highly regarded options (with links to their sites):
- 1Password: A user-friendly, feature-rich manager that consistently ranks at the top for its security and design. 1Password is often rated a top choice among premium password managers. It supports all major platforms (Windows, macOS, Linux, iOS, Android) and offers convenient features like Watchtower, which warns you of weak or compromised passwords and other security issues. 1Password doesn’t have a free tier, but it offers family plans and has a solid reputation for protecting data with end-to-end encryption.
- Bitwarden: An open-source password manager that has quickly become a favorite, especially because it offers a powerful free version. Bitwarden’s free tier allows unlimited passwords on unlimited devices – more than enough for most users – and has features like syncing and autofill. It’s lauded for its transparency (the code is openly auditable) and strong security model. If you want a no-cost solution or prefer open-source software, Bitwarden is an excellent choice.
- Dashlane: A well-known password manager with a focus on ease of use and extra features. Dashlane is a feature-packed option – it has a straightforward interface (so managing passwords isn’t a chore) and touts strong security, including dark web monitoring for your leaked info on premium plans. In fact, Dashlane “is keen to pitch its strong security credentials as a leading feature” while also being easy to navigate. It offers cross-platform apps and even a built-in VPN in some plans. Dashlane has a free tier (limited to one device) and paid plans with more functionality.
- NordPass: A newer contender created by the team behind NordVPN, it combines a simple interface with robust security. NordPass uses powerful encryption and has all the essentials – password generation, autofill, data breach scanning, etc. Notably, NordPass offers a free tier with unlimited passwords (the only limitation is you can only be logged in on one device at a time). Its premium version adds features like password health reports, up to 6 active devices, and item sharing. NordPass is a great option if you’re already in the “Nord” ecosystem or want an intuitive manager that covers the basics well.
(Other reputable password managers include LastPass, Keeper, RoboForm, KeePass, and Proton Pass, among others. The four above, however, represent a mix of popular choices for different needs – from free/open-source to premium offerings.) Each manager has its own style and features, but any good password manager will significantly improve your security by enabling strong, unique passwords everywhere without the headache of remembering them all.
Tips for Securely Using a Password Manager
Using a password manager is a smart move, but you should still follow some best practices to maximize security:
- Protect your master password: The master password to your vault is the one password you must make very strong (and never reuse anywhere else). Use a long passphrase or complex password – experts recommend at least 12–15 characters, ideally a mix of words or a sentence that you can remember but others can’t guess. Never share this master password with anyone, and do not write it on a sticky note on your monitor (if you must write it down, keep it in a very secure place like a home safe).
- Enable 2FA on the password manager: Most standalone password managers support two-factor authentication for unlocking your vault (for example, requiring a one-time code from your phone in addition to the master password). Enable this feature if available. It adds a significant safeguard – even if someone somehow got your master password, they still couldn’t access your vault without the second factor.
- Use a reputable, zero-knowledge manager: When choosing a password manager, use one that employs end-to-end encryption and a zero-knowledge architecture (meaning even the company cannot see your passwords). All the options listed above meet this criteria. A good manager will encrypt your data locally and only you can decrypt it. Many also have security features like notifying you of breached websites or flagging weak passwords – take advantage of those features.
- Keep the software updated: Whether you use a browser-based password manager or a standalone app, install updates regularly. Updates often patch security vulnerabilities or improve how the manager defends your data. Similarly, use strong device security (like a phone PIN or computer login password) since your password vault is only as safe as the devices you access it from.
- Leverage the password manager’s features: Let your manager do its job! Use the built-in password generator to create new passwords rather than coming up with your own. The random passwords managers generate are far stronger than what most humans devise. Also pay attention to any security alerts the manager provides (for example, if it flags that you have duplicate passwords or ones that appear in breaches). Many managers have an audit or “security checkup” – run it periodically to improve your vault’s health.
- Plan for emergency access: One risk of password managers is if you forget your master password, you could lock yourself out. Many services cannot reset your master password for you by design (to preserve zero-knowledge security). To avoid getting locked out, make use of any emergency recovery options. For instance, 1Password provides an Emergency Kit (a PDF with your key details and a place to write your master password) – you should print that and store it securely. Some managers let you set up an emergency contact who can get limited access if you’re incapacitated. At minimum, have a secure backup of your master password somewhere (like a sealed note in a safe) so that you or your loved ones can recover your accounts if needed.
By following these tips, you greatly reduce any risks associated with using a password manager. The idea is to add convenience without introducing a single point of failure. A well-chosen and well-protected password manager will keep your credentials safe even if the manager company itself is targeted.
What to Do if Your Password Is Found in a Breach
Discovering that one of your passwords has been leaked (whether through the 16 billion credential breach or any other incident) can be alarming. Don’t panic – take immediate action with the following steps:
1. Change the affected password immediately. Go to that account and update the password to a new, strong and unique one (ideally using your password manager to generate something random). This cuts off the attackers’ access if they haven’t used it yet.
2. If you reused that password on any other accounts, change those too. This is critical – a leaked password is essentially public knowledge to hackers, so you must assume any account using it is compromised. Change every instance of that password to a distinct new password. Going forward, avoid reuse (see Section 4) so one breach won’t have such a broad impact.
3. Enable two-factor authentication if not already enabled. Adding MFA can prevent the attackers from using the stolen password to break in, even if you haven’t gotten around to changing it everywhere. For the affected account and any other important accounts, turn on 2FA (with an authenticator app or SMS) as an urgent protective measure.
4. Check account settings and activity. Once you secure the account with a new password, review your account for any suspicious changes: unknown login locations, unfamiliar linked devices, forwarding rules (for email accounts), etc. If you find evidence that someone accessed the account, take additional steps like logging out all active sessions, contacting the service’s support, or in extreme cases temporarily disabling the account.
5. Be alert for related scams. After a large breach, affected users may be targeted by phishing emails or scam calls. For example, you might get an email pretending to be from the breached service, urging you to click a link to “verify your account.” Or scammers might use leaked personal info to craft convincing fraud attempts. Keep your guard up. Remember that legitimate companies won’t ask for your password via email. When in doubt, contact the company directly through their official website/app. (It’s also wise to monitor your financial statements and credit if the breach included any financial or personal data.)
6. Consider a password manager and overall security refresh. A breach can be a good catalyst to improve your security hygiene. If this incident has you realizing you’ve reused passwords or used weak ones, now is the time to fix that systematically. Start using a password manager to generate and store strong credentials, and change your important account passwords to ones generated by the manager. This one-time effort will pay off massively in future security. Also ensure you have up-to-date antivirus/anti-malware on your devices (remember, much of the 16B breach data was gathered by malware on user computers – don’t let your device be the next victim).
Finally, if a particular service notifies you that your data was in a breach, follow their instructions as well. They might force a password reset or provide additional guidance. Stay informed through official channels (for example, the company’s blog or press releases for updates on the breach investigation).
Conclusion
Huge breaches like the “16 Billion Credential” incident can certainly be unsettling, but they are also an important reminder: we each have the power to protect our online accounts by practicing good password hygiene and security habits. In summary, make sure every account has a strong, unique password (and change any that don’t!), enable two-factor authentication wherever possible, and strongly consider using a reputable password manager to lighten the load and enhance your protection. By taking these steps, you dramatically reduce the risk that you’ll be the next victim, even when massive leaks occur.
Digital security is an ongoing process – it’s about layering defenses so that even if one layer fails (like a password leak), additional layers (MFA, unique credentials, timely alerts) keep you safe. While we can’t prevent breaches from happening, we can prevent attackers from easily exploiting our accounts when they do. With a bit of effort and the right tools, you can browse and communicate online with confidence that your accounts are locked down.
In the wake of this incident, let’s turn the alarm into action: strengthen your passwords, update your security settings, and spread the word to friends and family who might not be aware. By fostering a culture of good password practices, we make things that much harder for cybercriminals – and we take back control of our digital lives. Stay safe out there!
Sources:
- Cybernews – *16 billion passwords exposed in record-breaking data breach*
- Tom’s Guide – *16 billion password data breach: how to stay safe*
- Bank of ND (via Verizon DBIR) – *81% of breaches due to weak/reused passwords*
- Tom’s Guide – *Personal story: hacked due to reused password*
- Troy Hunt’s HaveIBeenPwned – *Breach checking and notifications*
- Cybernews – *How to create a strong password (2025 guidelines)*
- TechRadar – *Best Password Managers 2025 (overview of 1Password, Bitwarden, Dashlane, NordPass)*
- Canadian Centre for Cyber Security – *Password Manager Security Tips*