Can Someone Hack Me With My IP Address?
Updated • 22 min read
You just used a tool to find your IP address – a string of numbers – and now you're wondering if someone could use it to hack you. It's a common concern in our connected world. In this guide, we'll break down what an IP address is, what risks (if any) it exposes you to, and how you can protect yourself. Let's dive in with clear explanations, real-world examples, and actionable advice, so you can feel secure about your online privacy.
Understanding IP Addresses
Your IP (Internet Protocol) address works like a digital home address for your device. Just as the post office uses your street address to deliver mail, the internet uses your IP address to send the right data to your computer or phone. Every device that goes online – your phone, laptop, smart TV, even your printer – gets an IP address assigned so it can communicate on the internet.
There are two main types of IP addresses to know about: public (external) IPs and private (internal) IPs. The public IP is assigned by your Internet Service Provider (ISP) and is what websites and other computers on the internet see. Think of it as the address of your home network. The private IP exists within your local network (your Wi-Fi or Ethernet) and is used so your router can direct traffic to the right gadget (computer #1 vs. computer #2, etc.). If you have a home router, all your devices share the one public IP outwardly, while each device has a unique internal IP that only matters inside your home. This means an outsider on the internet generally only knows the address of your router, not the individual IP of your laptop or phone behind it.
IP addresses come in two flavors: IPv4 and IPv6. IPv4 addresses are the classic numbers like 192.54.23.14 – four sets of numbers up to 255. With billions of devices online, IPv4 started running out of unique addresses, so IPv6 was introduced, with longer strings of numbers and letters (e.g. 2001:0db8:85a3::7334) to offer almost unlimited addresses. For our purposes, both serve the same role of identifying your device online.
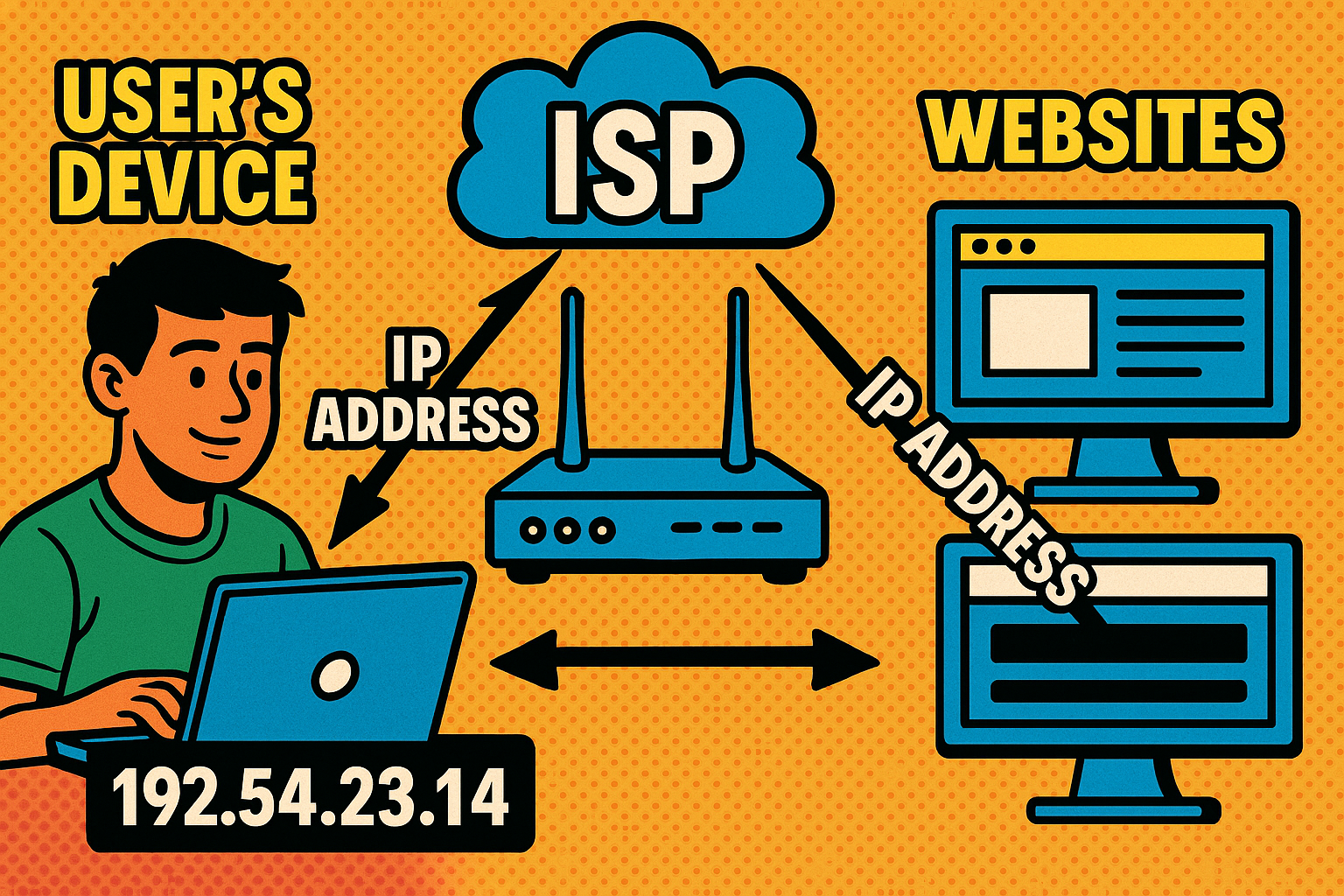
In short, your IP address is a necessary part of internet communication. But having an IP address is not secret or inherently dangerous – every website you visit sees your IP, and every online game you play uses IP addresses. The key question is what someone malicious can do if they specifically know your IP. Let's explore that next.
Potential Risks
What can an attacker or snoop do if they have your IP address? While an IP address alone is not a skeleton key to all your data, there are a few possible threats to be aware of:
- Find Your General Location: An IP address can reveal a rough geographic area. Usually this means the city or region and ISP you use, not your exact street address. For example, if someone has your IP, they might determine what city you’re in. In one real-world case, an online gamer got revenge on a rival by using the rival’s IP to find his approximate location and call in a false emergency (a dangerous prank known as “swatting”). This showed how an IP could be abused to approximate where you live and facilitate harassment. The good news is that the location data from IPs is fairly imprecise – it might point to your city or a nearby town, but it won’t pinpoint your door. Truly finding your exact address usually requires more personal information or cooperation from the ISP (which law enforcement can obtain, but random hackers cannot).
- Overwhelm Your Network (DDoS Attack): If someone is particularly unhappy with you online (say, in a gaming scenario), they might use your IP to flood your internet connection with traffic. This is called a Denial-of-Service (DoS) attack, or specifically a Distributed DoS (DDoS) when done from many machines. The attacker bombards your IP address with so much data that your home internet equipment can't handle it, knocking you offline. Even popular streamers have experienced this — for instance, Twitch broadcaster xQc had to end a livestream after attackers obtained his IP address during a game and launched a DDoS attack on his connection. While extremely annoying, a DDoS attack doesn't expose your personal data; it just temporarily cuts off your internet access. (It’s like clogging someone’s phone line by incessantly calling – disruptive, but not a breach of the phone itself.)
- Port Scanning and Exploiting Vulnerabilities: Think of your IP address as your house’s front gate on the internet. Behind the gate, you might have several doors (ports) leading into the house – for services like web servers, gaming servers, or remote desktop. If an attacker knows your IP, they might “knock” on all those doors to see if any are open. This process is called port scanning. Most home users don’t deliberately open any ports to the internet, so in many cases the scans find all doors locked. However, if you do have a poorly secured service exposed (or your router itself has an unpatched security flaw), an attacker could discover that and attempt to break in. This kind of reconnaissance is a common first step for skilled hackers and penetration testers. For example, an attacker might learn from a scan that you run Windows, and then try to use a known Windows bug to access your system. The vast majority of the time, if your system and router are up to date and you haven’t knowingly exposed any services, these probes will not succeed. But it’s a reminder to keep devices updated – just in case.
- Targeted Scams or Phishing: Knowing your IP can help a bad actor refine their scams to seem more believable. Since your IP reveals your ISP and general region, scammers might impersonate your internet provider or a local service. For instance, they could send a fake email or call pretending to be from YourISP Co. saying there's an issue with your account, to trick you into giving up sensitive info. They might reference your city to make it sound legit (“This is YourISP Co. for the \[Your City\] region...”). Cybercriminals have been known to spoof communications from a victim’s ISP once they know the IP/ISP, making the victim more likely to trust the scam. Additionally, if attackers see your IP in online games or forums, they might combine it with other clues to send more personalized fraudulent messages (“Hey, I saw you live near — we have a delivery for you...”). The IP on its own doesn’t give away your name or contact info, but in the hands of a scammer it can be one puzzle piece to craft a more convincing con.
- Service Restrictions and Bans: This is less about hacking you and more about causing mischief. An attacker could take your IP and try to get it banned from certain websites or games. How? By using your IP (or spoofing it) to make trouble on those services – for example, spamming or violating rules – so that the service bans that IP. This could result in you being temporarily blocked from a site or game through no fault of your own. This kind of harassment is uncommon but does happen, especially in online gaming communities where “IP banning” a known troublemaker is routine. If your IP got falsely flagged, you might suddenly find yourself unable to access a favorite service until you change IPs or convince the admins it wasn’t you.
\[Real-World Note: Police have advised people who are worried about swatting or DDoS attacks to take precautions like hiding their IP address with a VPN. We'll talk about prevention in a moment.\]
As you can see, most IP-related threats involve either harassment, inconvenience, or setting the stage for further hacking. Just knowing an IP doesn’t automatically give someone full access to your device or accounts. In fact, there are a lot of things an attacker cannot do with only your IP, which we'll clarify next.
*What Attackers Can’t Do*
It’s important to separate the myths from reality. Here are some common fears about IP addresses – and why you shouldn’t lose sleep over them:
- Hack Your Device Just by Knowing Your IP: Simply knowing your IP address does not give someone magical entry into your computer. An IP by itself is like knowing your street intersection without the keys to your house. “IP addresses are not very dangerous when a malicious user knows them,” as one security expert noted – thinking that an IP alone grants full access is a myth often spread by pranksters trying to sound scary. In practice, an attacker would also need a vulnerable service or open port on your device to actually hack in. No open ports or no vulnerabilities means no easy way in. So, if your system is secured and up-to-date, knowing your IP gets a hacker no further than knowing your apartment building’s name gets a burglar inside your locked apartment.
- Steal Personal Information (Just from IP): Your IP doesn’t contain your name, email, or other private details. All someone can glean is the ISP and a rough geographic area. They can’t directly learn who you are or what you’re doing just from the IP alone. For example, an IP might tell someone “This user is in or near Kansas City, using Comcast internet.” It does not say “This IP belongs to John Smith at 42 Maple Street who loves cat videos.” Attackers would need to link your IP with other info (through social engineering, data breaches, etc.) to get personal data. Even your internet provider won’t hand over customer details without proper legal process. So, while an IP can aid someone’s reconnaissance, it’s not an automatic privacy breach on its own.
- Pinpoint Your Exact Location: As mentioned, IP-based geolocation is imprecise. It might narrow you down to a city or region, but it won’t give away your door number or exact coordinates. In many cases, the location might even point to your ISP’s regional office or a neighboring town. You’ve probably seen websites guess your location from your IP and get it slightly wrong – that’s how unreliable it can be. So an IP address isn’t a GPS signal. Attackers can’t send a missile to your house or show up at your home just using an IP alone. (They’d need far more specific info for that, which an IP by itself doesn’t provide.)
- Access Your Online Accounts: Some people worry that if a hacker has their IP, they could somehow hijack banking logins, email sessions, or accounts left logged in. Rest assured, that’s not how it works. Online accounts are secured with passwords, authentication tokens, cookies, etc. Knowing your IP doesn’t grant access to any of those. One discussion on an information security forum put it clearly: “Merely knowing your public IP address would not allow \[attackers\] to log into any website” you’re logged into. Could an extremely skilled hacker use your IP as one element to attempt a sophisticated attack? Possibly, but they’d still need a vulnerability to exploit or to trick you into installing malware. They can’t just type your IP into a magic hacking program and instantly start controlling your computer or reading your Facebook messages. In short, your accounts and data are not laid bare simply by your IP being known.
To sum up, an IP address by itself is not an all-access pass for hackers. Think of it as knowing someone's phone number – it opens certain possibilities (like calling repeatedly or attempting scams) but doesn't let you automatically tap their calls. As long as you haven't neglected basic security (firewalls, updated software, etc.), an IP address alone cannot reveal your personal info or let someone take over your system. So if you hear an ominous “I have your IP, I'm gonna hack you,” take it with a grain of salt. Next, we'll move on to how you can bolster your defenses and avoid even the limited risks that do exist.
How to Protect Yourself
Even if the dangers of someone knowing your IP are relatively limited, it's still wise to take precautions. Good news: protecting your IP address and network doesn’t have to be difficult. Here are some effective steps:

- Use a VPN (Virtual Private Network): A VPN service masks your real IP address by routing your internet traffic through a server elsewhere in the world. To any outsider, it looks like the VPN server’s IP is the one doing the connecting, not yours. This is a powerful way to stay private online – cybercriminals can’t target you if they can’t even find your true IP. VPNs also encrypt your data, adding an extra layer of security. Many privacy-conscious users keep their VPN on whenever they’re online, which effectively makes your IP address a moving target that changes to a different location each time.
- Enable Your Firewall and Router Security: Think of a firewall as a bouncer for your device or network – it blocks unwanted incoming connections. Make sure you have a firewall active on your computer (Windows and macOS have built-in firewalls, just ensure they're enabled). Your router also acts as a hardware firewall since it by default stops unsolicited incoming traffic. Keep your router’s firmware up to date and change the default admin password on it (many attacks on routers happen simply because people leave “admin/admin” as the login\!). A properly secured router will fend off most random port scans or intrusion attempts from the internet.
- Improve Privacy Settings on Apps: Some apps or services can leak more info than you realize. For example, older versions of Skype allowed people to obtain a user's IP address by simply adding them as a contact. Check the settings of any messaging, VoIP, or gaming apps you use – enable privacy modes that hide your IP or only share it when necessary. Also, be cautious about accepting direct peer-to-peer connections from strangers in applications; wherever possible, use an intermediary server. While adjusting these settings won’t make your IP invisible, it can prevent easy access through certain apps.
- Be Wary of Suspicious Links and Emails: Since attackers may try to trick you into revealing more info or installing malware, practice good cyber hygiene. Don’t click on random links sent to you, don’t download unknown attachments, and don’t respond to unsolicited emails asking for personal details. This helps you avoid phishing traps that could expose more than just your IP (like actual passwords or installing backdoors). Remember that just visiting a website reveals your IP, so only go to trusted websites. Use a reputable ad-blocker to reduce the chance of malicious ads harvesting your data. In short, stay on guard online just as you would offline with strangers.
- Keep Software Updated: Many attacks that start with knowing an IP address still rely on outdated software to succeed. For instance, if you haven’t updated your operating system or router firmware in years, there may be known vulnerabilities that hackers can exploit remotely. Regular updates patch these holes. So update your computer, phone, and router firmware whenever updates are available. This greatly diminishes the chance that an IP scan turns up a weakness.
- Consider Changing Your IP: If you ever suspect your IP is being abused – say someone is DDoSing you or harassing you – one quick fix is often to change your IP address. Many home internet connections use dynamic IPs that change periodically, or can be changed by simply rebooting your router. Turning your router off for a few minutes and then back on will often assign you a fresh IP from your ISP. This is like changing your phone number on a pesky caller – their info becomes outdated. You can also request a new IP from some ISPs if needed. Changing your IP stops ongoing attacks tied to your old one, and the attacker loses track of you (at least until they somehow discover the new address, which may not be easy).
By following these steps, you greatly reduce the already-small chances of anything bad happening via your IP address. For instance, in the swatting example mentioned earlier, the police specifically recommended using a VPN or proxy to hide your IP while gaming, to prevent trolls from finding your location. A combination of smart software tools (like VPNs and firewalls) and good browsing habits will keep you safe.
Advanced Risks (ARP and IP Spoofing)
For those interested in deeper technical risks related to IP addresses, let's briefly touch on two advanced concepts: ARP Spoofing and IP Spoofing. These are not everyday threats for most home users, but they're good to understand in context.
- ARP Spoofing (ARP Poisoning): This is an attack that can occur on local networks (like if you're on public Wi-Fi or a shared office network). ARP stands for Address Resolution Protocol – it’s how devices on a local network map IP addresses to physical MAC addresses. In an ARP spoofing attack, a hacker on the same network sends fake ARP messages to trick your computer and the network router. The goal is to make your computer believe the hacker’s machine is the router, and vice versa. This puts the hacker in the middle of your traffic – a classic man-in-the-middle attack. Important: ARP spoofing only works if the attacker is on your local network. Someone can’t do this to you over the internet at large; they need to be within the network you're connected to (or have breached it somehow). To defend against ARP spoofing, avoid using untrusted networks (like unknown public Wi-Fi without a VPN), and ensure websites you use employ encryption (HTTPS) so even if someone intercepts data, it's gibberish to them. Modern network switches and some security software can also detect and block ARP poisoning attempts.
- IP Spoofing: This is almost the opposite scenario – instead of targeting you by using your IP, the attacker pretends to be you (or someone else) by faking an IP address. In IP spoofing, a hacker forges the source IP field in the packets they send out, so it looks like the data is coming from a different IP address than theirs. Why would they do this? One common reason is in certain types of DDoS attacks: by spoofing IPs, they can hide the origin of the attack or trick other systems into responding to the fake IP (causing traffic to flood a target). Another malicious use is framing someone – for instance, making bad activity appear to come from your IP address. If a hacker carries out an illegal hack or launches attacks while spoofing your IP, it could direct attention or blame toward you. In fact, security experts warn that IP spoofing can be used to impersonate a victim’s device and perform bad actions in their name, potentially including crimes. The good news is that truly framing someone with IP spoofing is easier said than done; it might fool some logs, but a proper investigation can often unravel the deception (since the perpetrator can’t receive responses at the fake IP, the interaction is one-way and detectable). Moreover, many online services have protections against IP spoofing (for example, they may require a handshake that a spoofed IP can’t complete). Regardless, it’s a reminder that IP addresses can be manipulated – so if you ever hear that “XYZ crime was done from your IP” and you know you didn’t do it, IP spoofing is a possible (though rare) culprit.
In summary, ARP spoofing and IP spoofing are advanced techniques that skilled attackers use in specific scenarios. ARP spoofing involves an attacker on your local network intercepting your traffic by pretending to be your router. IP spoofing involves an attacker masquerading as another IP (possibly yours) to hide their identity or implicate someone else. These are not the kinds of threats most individuals need to worry about day-to-day, but they underscore the importance of secure networks and vigilant system admins who can detect such tricks.
For the average user, the practical takeaway is: use encrypted connections and be cautious on shared networks (to thwart ARP attacks), and know that internet authorities (like websites or ISPs) have ways to tell when IPs are being spoofed in malicious ways, so you generally won’t be held accountable for something you clearly didn’t do.
Static vs. Dynamic IP Addresses
You might have heard these terms: static IP and dynamic IP. It’s worth understanding the difference, because it can affect how you manage your IP privacy.
- Static IP Address: “Static” means unchanging. If you have a static IP, your ISP has assigned you an address that never or rarely changes. This is common for businesses, servers, or anyone who requested a static address. The upside of a static IP is reliability – for example, if you run a website or need to remotely access your home camera, a static IP is a consistent point of contact. However, static IPs have some privacy and security downsides for everyday users. Since the address doesn’t change, if it becomes known to attackers, they can target it over and over. It essentially puts a permanent bulls-eye on your network’s location. Static IP users can be easier to track and locate online, and are more vulnerable to repeated attacks like DDoS if someone harbors ill intent. In fact, one security comparison noted that static IPs are more hackable in the sense that a hacker can keep probing the same target, and static users might be easier to pinpoint in the real world. Static IPs also can be a bit more costly (some ISPs charge extra for them). If you have a static IP for a good reason, just be sure to use the protective measures we discussed (VPN, firewall, etc.) since that IP is tightly tied to you.
- Dynamic IP Address: Most home users have dynamic IPs by default. “Dynamic” means it changes from time to time. Your router might get a new IP lease from the ISP every time you reboot, or every few days/weeks automatically. The benefit here is that it’s harder for anyone to consistently track you or harass you, because your address isn’t fixed. If a troublemaker learns your IP one day, there’s a decent chance it will be different by next week (or even the next day) without them knowing. Dynamic IPs thus “reduce the risk of DDoS attacks and are harder to target,” as a VPN provider summary puts it. They add a layer of obscurity simply by rotating. From a security standpoint, this is handy: even if your IP appears on some spammer’s radar, it might become stale soon. The main downside – which isn’t a big deal for most – is that if you needed to remote into your home network, or if a service is set to trust your IP, the changing address can be inconvenient. But for typical browsing, streaming, gaming, you won’t notice the change. Dynamic IPs are also usually free and standard with your internet plan, whereas static often requires a request or fee.

Which should you use? For most people concerned about privacy and hacking, dynamic IP is perfectly fine and often safer. You get a bit of built-in rotation that makes you a moving target. Static IP is useful if you have specific needs (like running a server or needing to allowlist your home IP for certain services), but it comes with the responsibility of guarding that known address. If you do have a static IP, you might want to be extra cautious about using a VPN when doing sensitive activities, since your IP is essentially a consistent identifier for you.
Regardless of static or dynamic, remember that any IP address only reveals limited info (region and ISP) – not your personal details. And no matter which type you have, the security fundamentals remain the same: use good network hygiene to keep potential attackers at bay.
Conclusion
Finding out your IP address can be a bit like discovering your phone number is public – a little alarming at first. But as we've seen, someone hacking you outright using just your IP is highly unlikely. Your IP address alone usually cannot hurt you without additional weaknesses to exploit. The real risks (such as DDoS, crude location tracking, or targeted scams) can be mitigated with common-sense steps: keep your system updated, use a VPN or firewall, and stay alert online.
The internet is built on IP addresses, and every day you share yours with websites and services in order to use them. Thankfully, this is normally safe and routine. By understanding what your IP does and doesn’t reveal, and by taking a few precautions, you can enjoy the internet without fear that every stranger who knows your IP is about to break into your life. In short, treat your IP address with the same cautious respect you’d treat your phone number or home address – don’t broadcast it needlessly – but don't panic about it either. With the knowledge from this guide, you can confidently answer “Can someone hack me with my IP address?” – and realize that the answer is, for the most part, no – as long as you take basic steps to stay secure. Stay safe and happy browsing!
References: (All links accessed on May 27, 2025)
1. Norton – *What can someone do with your IP address?*
2. News5 Cleveland – *Medina County “swatting” incident – gamers and IP addresses*
3. Sportskeeda – *Twitch streamer xQc hit by DDoS after IP leak*
4. Aura – *10 risks someone can do with your IP address*
5. Security.org – *What someone can (and can't) do with your IP*
6. Keeper Security – *IP address alone will not allow hackers in*
7. Security StackExchange – *Expert answer debunking IP address hacking myth*
8. Imperva – *What is ARP Spoofing (Man-in-the-Middle explained)*
9. Imperva – *What is IP Spoofing*
10. CyberGhost VPN – *Static vs Dynamic IP (security differences)*
11. Security.org – *Static vs Dynamic IP guide*